So work stuff now….
…and the Friday afternoon before a Bank Holiday…and what drops into my inbox….
….something very exciting! At least that is what I have been telling all my customers and prospective customers for the last few weeks.
Smoothwall’s giant leap into the world of extended BYOD support is just around the corner.
And the inbox message was confirmation that the pre-release phase is now being entered into. We are into Staff release.
This was received with the exclamation to the relevant product manager…that I do have a life…things to do and people to see over the extended weekend….but with two nights of baby-sitting to do…it was inevitable that the new shiny update would get spun up….and a battle with a new implementation method would commence.
So let me offer a bit of explanation….this is upcoming Main 60 update to Smoothwall, and offers two main functional improvements. Namely:
- WPA Enterprise support. Version 2 is preferred, but legacy support for version 1 is included. Brand spanking new Smoothie RADIUS server and 802.1x support.
- Improved SNI support for un-supporting websites.
Apart from that it’s sweet. Forget messing around with SSL login pages, mis-behaving applications and double sign-in to your guest Wifi setup.
If your AP or wireless LAN controller infrastructure is 802.1x compliant with support for PEAP and MSCHAPv2 you are good to go.
So on Friday night…I thought I would have a go at attempt number one….knowing full well that it would probably end up being a swing and a miss.
Here’s what I did:
- Naturally backed and snap-shotted everything in sight.
- Main external component was the Wireless AP. I disassociated my Apple AirPort Express (first generation...the one on a plug) from the existing WLAN, as it was only being used as an extender.
- Created a new BYOD VLAN on the physical and virtual switching infrastructure. Two ports, one physical for the AP and one virtual for the Smoothie.
- Shutdown the virtualised Smoothwall UTM/AF install for the network, added a new virtual NIC to the VM. Booted into CLI and configured.
- Went to WebUI to configure DHCP/DNS and External access.
- Navigated to the new Service -> Authentication - WPA Enterprise section.
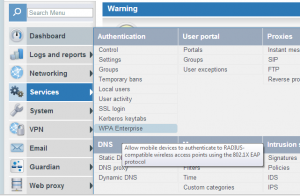
- Created RADIUS server, configured shared secrets and created new Access Point definition.
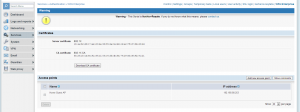
- Implemented a core authentication transparent proxy on the new network interface.
- Airport configuration now. And I have to say that this went very well. Despite the lack of compatibility documentation around MSCHAP, I needn't have worried. A quick config using AirPort Configuration Utility for both Mac and PC, and I was up and rolling. One note about AirPort, as it uses Bonjour...you'll need to be on the same subnet as the Smoothie's BYOD network. The correct feature support and ease of implementation make the Apple AirPort Express a strong candidate for BYOD implementation....and naturally offers great iOS integration for all your corporate and educational iPad estates.
- In the back-end, I was authenticating to a pre-existing Windows 2008 R2 domain. As I was serving AD users on the new 802.1x authenticated network, AD security groups and group mappings need no further integration. It just worked.
Very impressive….now the guest user experience to logon to the guest Wifi is simple. Fire-up the device…connect with WPA Enterprise….provide AD login credentials….either guest or know user….and then use. Maybe deploy the HTTPS Inspection CA cert via email if necessary.
But this then gives the user seamless app authentication…persistent browsing sessions….full user monitoring and control. Deep at its heart is the Smoothie’s Core authentication system, meaning full “Who” rule support through out the interface and rule bases…for all the new BYOD network users. Work great with devices your are unable to manage or set proxy settings…true transparent authentication.
Imagine giving someone a quick set of AD credentials and being able to control every aspect of their Internet and e-content usage. Bandwidth, times and quotas, exceptional categorisation and full visibility of usage.
Last thing to say about this deployment is the documentation is great. Puts you under no illusions [that’s what this post is for ;-) ], is concise and straight forward.
So in summary, when it goes Gold and is released to your target group….give your BYOD network a functional leg-up….and revel in Smoothwall’s Main 60 release.
P.S. If you think we are done….just wait until our reporting update comes out….my next work related post may be called: “Enter the Woodshed”!
✴️ Also on Micro.blog